SASE Has 40% Adoption Rate. Here’s What It Means
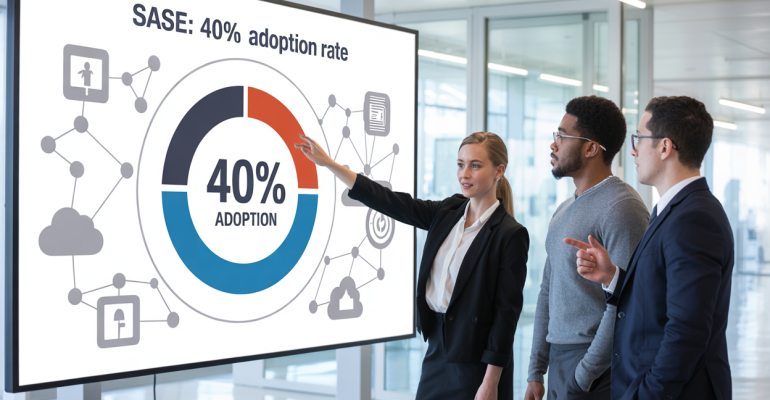
SASE Has 40% Adoption Rate. Here’s What It Means
SASE adoption has hit a major milestone, with 40% of enterprises now actively implementing this cloud-native security framework. This rapid growth signals a fundamental shift in how organizations approach network security and digital transformation.
This article is for IT leaders, security professionals, and business executives who need to understand what this SASE adoption rate means for their organizations and the broader cybersecurity landscape.
We’ll explore why SASE market growth has accelerated so dramatically, examining the core security benefits that are driving widespread adoption. You’ll also discover the operational advantages that make SASE architecture attractive to enterprises moving away from traditional point solutions. Finally, we’ll cover the key implementation strategies that successful organizations use to deploy SASE effectively while maximizing their return on investment.
Understanding SASE’s Current Market Position and Growth Trajectory
40% Enterprise Adoption Rate by 2024 Represents Massive Growth
The SASE adoption rate has reached remarkable heights, with projections indicating that at least 40% of enterprises will have explicit strategies to adopt SASE by 2024. This figure represents an extraordinary transformation in how organizations approach network security and connectivity. The massive growth trajectory demonstrates that SASE has moved from a niche solution to a mainstream strategic imperative for modern enterprises seeking comprehensive security frameworks.
Evolution from Less Than 1% Adoption in 2018 to Strategic Priority
The evolution of SASE market growth presents one of the most dramatic technology adoption stories in recent enterprise history. Starting from less than 1% of enterprises having SASE strategies at year-end 2018, the technology has experienced unprecedented acceleration. This meteoric rise from minimal adoption to becoming a strategic priority for 40% of enterprises by 2024 illustrates how quickly organizations recognized the value proposition of integrated network security solutions.
The transformation reflects a fundamental shift in enterprise thinking, where traditional perimeter-based security models proved inadequate for increasingly distributed workforces and cloud-first architectures. Organizations that initially viewed SASE as experimental technology now consider it essential infrastructure for maintaining competitive advantage in digital-first business environments.
COVID-19 Acceleration of Remote Work Driving SASE Demand
Worldwide COVID-19 social distancing directives significantly accelerated remote work adoption, creating an unprecedented catalyst for SASE demand. The pandemic permanently altered internet traffic patterns, service provider infrastructures, and enterprise connectivity requirements. Organizations suddenly faced the challenge of securing and managing access for distributed workforces operating from countless locations outside traditional network perimeters.
This disruption exposed critical vulnerabilities in legacy security architectures that were designed for centralized office environments. The urgent need to support remote work while maintaining security standards drove many enterprises to fast-track their SASE implementation plans, compressing typical multi-year adoption cycles into months.
Single-Vendor SASE Solutions Growing from 5% to 20% by 2023
The trend toward comprehensive single-vendor SASE solutions demonstrates growing enterprise preference for integrated platforms over fragmented point solutions. Gartner expects that by 2023, 20% of enterprises will have adopted single-vendor SASE solutions encompassing Secure Web Gateway (SWG), Cloud Access Security Broker (CASB), Zero Trust Network Access (ZTNA) services, and branch Next-Generation Firewall capabilities. This represents a four-fold increase from less than 5% adoption in 2019.
This consolidation trend reflects enterprise desire to reduce complexity, improve interoperability, and achieve better total cost of ownership through unified SASE architecture. Single-vendor solutions offer streamlined management, consistent policy enforcement, and simplified troubleshooting compared to multi-vendor environments requiring complex integrations.
Core Security Benefits That Drive SASE Adoption
Seamless Zero Trust Implementation Reduces Data Breaches by 50%
SASE’s security framework ensures seamless zero-trust implementation, fundamentally transforming how enterprises approach network security. By verifying users and devices before granting access, SASE integrates security policies directly into the network fabric, creating an inherent security-first architecture. This approach represents a significant departure from traditional perimeter-based security models.
The power of SASE lies in combining Zero Trust Network Access (ZTNA), Secure Web Gateways (SWG), and Cloud Access Security Brokers (CASB) into a unified platform. This integration minimizes attack surface while offering granular controls that enable precise access management. Organizations implementing zero-trust architectures through SASE have experienced data breaches dropping by as much as 50%, demonstrating the tangible security benefits of this comprehensive approach.
Enhanced Data Sovereignty and Compliance Management
SASE enhances data sovereignty and compliance by enforcing region-specific data handling and access policies, ensuring sensitive data is stored and processed according to local regulations like GDPR and CCPA. This capability becomes increasingly critical as organizations operate across multiple jurisdictions with varying regulatory requirements.
Through SASE, enterprises can reduce non-compliance risks and associated fines with precise control over data flow and access. The platform monitors compliance via integrated secure web gateways (SWG) and CASB, providing real-time visibility into data movements and access patterns. This integrated approach eliminates the complexity of managing multiple compliance tools while ensuring consistent policy enforcement across all network touchpoints.
Integrated Threat Intelligence for Real-Time Protection
SASE delivers integrated threat intelligence by combining advanced security tools including CASB, ZTNA, and SWGs with real-time global threat intelligence feeds. This convergence enables organizations to detect, analyze, and mitigate threats across the entire network infrastructure from a single platform.
The real-time nature of this threat intelligence integration allows for immediate response to emerging threats, significantly reducing the window of vulnerability that cybercriminals often exploit.
Advanced Threat Detection Against $4.88 Million Average Breach Costs
With the average data breach cost reaching an all-time high of $4.88 million in 2024—a 10% increase from 2023—organizations need robust defense mechanisms more than ever. SASE offers advanced threat detection capabilities, allowing quick detection and mitigation of emerging risks like malware, phishing, and Advanced Persistent Threats (APTs).
SASE applies AI-driven insights to analyze user behavior and traffic patterns, identifying anomalies that might indicate security threats. Continuous monitoring and automated responses enhance protection against evolving cyber threats, providing unified defense capabilities that adapt to the changing threat landscape. This proactive approach significantly reduces the likelihood of successful attacks and their associated financial impact.
Operational Advantages of SASE Architecture
Enhanced Network Visibility and Centralized Control
SASE architecture revolutionizes network visibility by consolidating monitoring tools into unified dashboards, providing organizations with real-time insights into user activity, data flows, and application usage. This centralized approach eliminates the fragmented visibility that traditional security architectures often create, enabling IT teams to maintain comprehensive oversight of their entire network infrastructure from a single pane of glass.
The advanced analytics capabilities embedded within SASE solutions continuously assess network traffic patterns, effectively eliminating blind spots that could harbor potential security threats. This constant monitoring facilitates early threat detection, allowing organizations to identify and respond to suspicious activities before they escalate into significant security incidents. Additionally, centralized policy enforcement through SASE architecture empowers security teams to make informed decisions based on comprehensive network intelligence, enabling rapid risk response and maintaining consistent security postures across all network segments.
Cost-Effectiveness Through Infrastructure Consolidation
Now that we understand the visibility advantages, the financial benefits of SASE implementation become equally compelling. SASE delivers substantial cost-effectiveness through infrastructure consolidation by replacing fragmented security tools with a unified cloud-delivered platform. This consolidation approach significantly minimizes infrastructure costs and operational overheads by eliminating the need for expensive hardware upgrades and reducing the complexity of managing multiple disparate security solutions.
The scalability inherent in SASE architecture allows businesses to adopt a pay-as-you-use model, ensuring organizations only invest in the resources they actually need. This strategic resource allocation capability enables companies to optimize their technology spending while maintaining robust security coverage. The elimination of redundant security tools and the reduction in hardware maintenance costs contribute to improved return on investment, making SASE an economically attractive solution for organizations seeking to modernize their network security framework.
Simplified Management Reducing IT Complexity
With cost benefits established, the operational simplification that SASE provides represents another crucial advantage. SASE architecture simplifies management and reduces IT complexity by unifying network and security functions into a single comprehensive framework. This integration significantly lessens organizational dependency on specialized IT teams while lowering overall operational complexity, allowing organizations to streamline their technology management processes.
The centralized management capabilities of SASE, combined with real-time threat intelligence, substantially enhance an organization’s response capabilities against emerging threats. This unified approach enables IT teams to focus on strategic initiatives rather than being consumed by day-to-day operational tasks. By automating routine processes and providing a single management interface for both network and security functions, SASE architecture reduces the administrative burden on IT staff while improving overall security effectiveness.
Improved Network Performance and User Experience
Previously established operational benefits naturally lead to enhanced performance outcomes. SASE improves network performance and user experience by optimizing data routing and reducing latency across the network infrastructure. This optimization ensures consistent, reliable connectivity for users regardless of their location or the applications they access.
The architecture enables faster access to cloud-based applications and services by intelligently routing traffic via the closest secure point of presence (PoP) and implementing intelligent path selection algorithms. This approach minimizes the distance data must travel, reducing latency and improving response times for critical business applications. The result is a superior user experience that supports productivity while maintaining the highest levels of security, making SASE architecture an essential component for organizations pursuing digital transformation initiatives.
Key Technologies Enabling SASE Success
Cloud-Native Architecture for Scalability and Flexibility
SASE technology fundamentally operates on a cloud-native architecture, representing a paradigm shift from traditional network security approaches. This cloud-native foundation ensures robust security for remote and hybrid environments while maintaining the scalability and flexibility that modern organizations demand. The architecture provides secure, scalable access to applications and data without compromising user experience or performance, making it particularly valuable for distributed workforces.
The purely software-defined nature of SASE services is specifically designed for cloud environments, offering unprecedented flexibility and data control for remote work and hybrid cloud setups. This software-defined approach eliminates the need for complex hardware deployments while providing centralized management and policy enforcement across all network endpoints.
Software-Defined WAN Integration
Software-Defined WAN (SD-WAN) represents a major component within SASE architecture, seamlessly integrating advanced networking capabilities with comprehensive security features. This integration allows organizations to optimize network performance while maintaining security standards across all network connections. SD-WAN technology within the SASE framework enables intelligent traffic routing, bandwidth optimization, and real-time network visibility, all while ensuring that security policies are consistently applied regardless of connection type or location.
Zero Trust Network Access and Secure Web Gateways
Zero Trust Network Access (ZTNA) and Secure Web Gateways (SWG) serve as essential components in the SASE technology stack, working together to implement comprehensive zero trust network access principles. These technologies continuously monitor compliance, detect emerging threats, and verify user identities before granting access to network resources. ZTNA ensures that no user or device is automatically trusted, regardless of their location or previous access history, while SWG provides real-time web filtering and threat protection for all internet-bound traffic.
Cloud Access Security Broker Capabilities
Cloud Access Security Broker (CASB) capabilities form an integral part of SASE implementation, working alongside ZTNA and SWG to provide comprehensive cloud security coverage. These capabilities enable organizations to enforce security policies consistently across all cloud applications and services while monitoring data flow in real-time. CASB functionality within SASE provides integrated threat intelligence, ensuring that security teams have complete visibility into cloud usage patterns and can respond quickly to potential security incidents across their entire cloud infrastructure.
Future Technology Trends Shaping SASE Evolution
AI-Driven Security for Enhanced Threat Detection
With the increasing sophistication of cyber threats, SASE technology trends are evolving to incorporate advanced artificial intelligence capabilities that fundamentally transform threat detection and response. AI-driven security within SASE architecture delivers real-time threat detection that operates continuously across all network touchpoints, analyzing vast amounts of data to identify anomalous patterns and potential security breaches as they emerge.
The integration of AI enhances incident response automation, enabling SASE platforms to automatically initiate protective measures without human intervention. This automation significantly reduces response times from hours to milliseconds, creating a more resilient security posture that adapts to emerging threats in real-time.
Advanced analytics powered by AI algorithms can predict vulnerabilities before they are exploited, providing organizations with proactive security measures rather than reactive responses. This predictive capability improves both accuracy and speed in mitigating evolving threats, ensuring that the secure access service edge framework stays ahead of increasingly sophisticated attack vectors.
5G Network Readiness and Edge Computing Integration
Now that we understand AI’s role in SASE evolution, the integration with 5G networks represents another critical advancement in SASE architecture. SASE technology is specifically designed for 5G network readiness, providing the infrastructure needed to secure ultra-low latency and high-speed 5G networks that are becoming the backbone of modern digital operations.
This 5G integration ensures seamless and secure connectivity for IoT devices, which are proliferating across industries and requiring robust security frameworks that can handle massive device populations. The SASE architecture’s ability to maintain security standards while supporting 5G’s enhanced capabilities makes it essential for organizations deploying next-generation connectivity solutions.
Edge computing integration becomes particularly crucial as organizations distribute computing resources closer to end users. SASE’s compatibility with edge computing environments ensures that security policies remain consistent regardless of where data processing occurs, maintaining the integrity of the zero trust network access model across distributed infrastructure.
Decentralized Data Security for Edge Environments
Previously established 5G and edge computing capabilities lead naturally to the need for enhanced decentralized data security. SASE architecture is adapting to the growing edge-computing trend by implementing security measures that protect data flows across distributed environments where traditional perimeter-based security models prove inadequate.
The framework ensures consistent policy enforcement across all edge locations, maintaining uniform security standards regardless of geographic distribution or local infrastructure variations. This consistency is crucial for organizations operating in multiple locations or serving global user bases through edge computing resources.
SASE’s evolution includes protecting sensitive information closer to where it is generated or accessed, reducing the risk associated with data transmission across long distances while maintaining compliance requirements. This localized security approach aligns with regulatory demands for data sovereignty and privacy protection in various jurisdictions.
Increased Convergence of Networking and Security Functions
With edge computing security considerations addressed, the future of SASE involves deeper convergence of networking and security functions as organizations seek to streamline operations and reduce operational complexity. This convergence represents a fundamental shift from traditional approaches where networking and security operated as separate functions with distinct management overhead.
The increased convergence leads to greater demand for holistic solutions that seamlessly address both security and connectivity issues within a single platform. This integration eliminates the need for multiple point solutions and reduces the complexity associated with managing disparate systems that often create security gaps at integration points.
Organizations benefit from this convergence through simplified management interfaces, unified policy enforcement, and reduced total cost of ownership. The streamlined approach enables IT teams to focus on strategic initiatives rather than managing complex integrations between multiple security and networking solutions, ultimately improving organizational agility and security effectiveness.
Best Practices for Successful SASE Implementation
Infrastructure Assessment and Gap Analysis
Begin with a comprehensive infrastructure assessment and gap analysis to evaluate your existing networking and security infrastructure. This critical first step involves identifying areas for consolidation and determining specific business needs like remote work security or compliance requirements. A thorough assessment reveals gaps in your current security posture and networking capabilities, providing the foundation for strategic SASE implementation decisions.
Strategic SASE Solution Selection Criteria
Strategically select a SASE solution by assessing providers based on essential criteria that align with your organizational needs. Evaluate security features including ZTNA (Zero Trust Network Access), CASB (Cloud Access Security Broker), SWG (Secure Web Gateway), and threat intelligence capabilities. Performance metrics such as low latency and high speed are crucial for maintaining user experience. Additionally, assess scalability options, cloud-native architecture, integration capabilities with existing systems, compliance adherence to industry standards, and comprehensive SLA support to ensure reliable service delivery.
Pilot Implementation and Performance Monitoring
Implement SASE through a carefully planned pilot project to test performance, security, and integration capabilities before committing to a complete rollout. Monitor key metrics including user experience, network latency, and threat detection effectiveness throughout the pilot phase. This approach allows you to validate the solution’s effectiveness in your specific environment while minimizing risk to the broader organization.
Integration with Existing Security Tools and User Training
Gather feedback from end users and IT teams to refine your implementation strategy before scaling to the broader organization, ensuring a smooth transition. Integrate SASE with existing security tools such as SIEM, identity management, and endpoint protection systems to ensure consistent policy enforcement, simplify centralized monitoring, and improve threat detection capabilities. Invest in regular user training and support for both IT teams and end users to minimize disruptions, boost user confidence, and foster a security-first mindset. Provide comprehensive guidance on policies and secure resource access through workshops and detailed documentation to maximize SASE adoption success.
The 40% adoption rate for SASE represents a fundamental shift in how organizations approach network security and performance. As enterprises continue their digital transformation journeys, SASE’s unified cloud-native architecture addresses critical challenges including remote work security, cloud application access, and regulatory compliance. The convergence of networking and security functions into a single platform not only reduces operational complexity and costs but also delivers enhanced threat protection through integrated zero-trust principles and AI-driven threat intelligence.
Organizations considering SASE implementation should begin with a thorough assessment of their current infrastructure and start with pilot deployments to validate performance and integration capabilities. With trends pointing toward increased AI-driven security, 5G readiness, and edge computing support, SASE positions businesses for future technological evolution while delivering immediate benefits in security posture, operational efficiency, and user experience. The question isn’t whether to adopt SASE, but rather how quickly organizations can strategically implement this transformative technology to maintain competitive advantage in an increasingly cloud-first business environment.